The History
As we evolved, we started practicing different ways of trade. In our earlier civilizations, we used the Barter system, which is the exchange of goods or services for other goods or services in return without using any medium for exchange. This concept of trading seemed to be a fitting solution initially. But, with this, the real value of goods and services couldn’t be measured to its actual worth. Hence, the Barter system was bound to fail.
Then came the centralized banks who acted as the main authority to facilitate trading and make it fairer. The concept of money was introduced. Money, in its physicality, can be a piece of metal, or a piece of paper with an organizational stamp, but the entity in itself doesn’t have as much value as people place on it. By establishing a central authority, we surely have ticked all the right checkboxes when it comes to trust and verification and also ease of transaction. But what if, the central authority turned rogue? Or what about transaction processing add-ons that comes along with it? What if the bank loses all the money which in-turn results in you losing your money?
These are some of the serious shortcomings that can potentially wreak havoc during the times of financial turmoil. With all the progress that we had achieved (and also considering the limitations of the previous systems), we stepped into the era of Digital Money. The Cryptocurrencies, Bitcoin for example, is a kind of digital/virtual currency which uses decentralized control and no central authority defines its worth. This article is not about Bitcoins and how to mine them, instead, it’s about the technology behind it.
That’s BLOCKCHAIN.
The Blockchain Technology
Blockchain is one such technology which has truly removed the need for a central authority of trust by adopting a decentralized design and also by storing data in a distributed fashion. These are essentially databases that are replicated over a peer-to-peer network.
The very first primitive form of blockchain was the datastructure ‘Hashtree’, also known as ‘Merkle Tree’ patented by the computer scientist Ralph Merkle in 1974. This initial representation of blockchain was then implemented in the year 1991 by a group of researchers to add digital timestamps to digital documents so that they could not be backdated or tampered.
However, this technology was left unused until the 2008 Financial Crisis which brought out the inherent limitations and flaws of banks and other financial institutions which majorly resulted in bankruptcy. In result of this fiasco, people wanted to eliminate the possibility of facing any such shortcomings in the future of being controlled by a central authority. This led to an unknown person or a group of people, by name Satoshi Nakamoto, implementing the blockchain technology to create the cryptocurrency Bitcoin in the year 2009. We’ll be discussing about this classic blockchain as constructed by Satoshi Nakamoto.
Blockchain is the technology; Cryptocurrency is its application.
Blockchain is a sequential chain of blocks that contains information. It’s a distributed ledger that stores transaction information within a distributed database that uses decentralized consensus. Think of it like a Google Sheet: whenever you share the sheet, it’s the copy that is being sent out and not the actual sheet itself. In this way, both the users have access to the shared copy and are aware of all the changes made to the sheet.
Or, you can relate a blockchain to a book, where individual pages are the blocks having transaction information, the page numbers indicating a continual sequence and the book itself being the blockchain and its also shared amongst the network so that everyone has a copy.
Everything’s a copy of a copy of a copy.
Let’s take the example of transferring funds between two people:
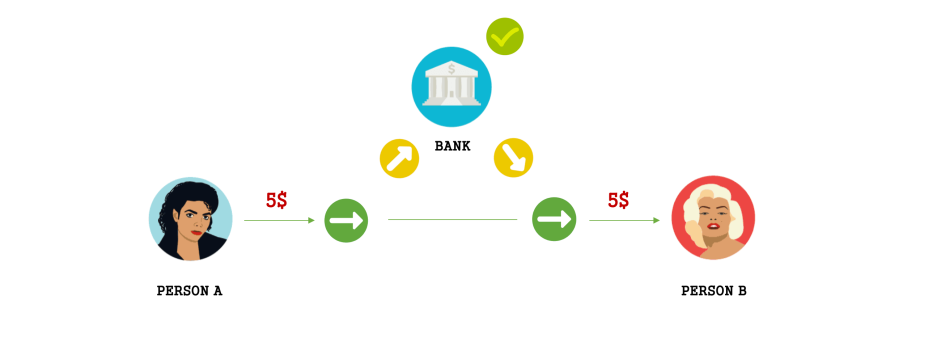
Fig 1: Bank Transaction
Case 1: In the above illustration (Fig 1), Person A initiates a transaction to transfer 5$ to Person B. The transaction here is being processed by a centralized authority i.e., the bank. While processing this transaction request, the bank typically does the following:
- Check if Person A has enough balance for the transaction.
- Check if Person B has a valid bank account.
- Coordinate between the banks incase Person A and Person B have different bank accounts.
Since they have to check, verify, initiate and process this entire transaction, they’ll also charge a transaction fee along with it. Also, the time that’ll take to complete this transaction is also considerably higher.
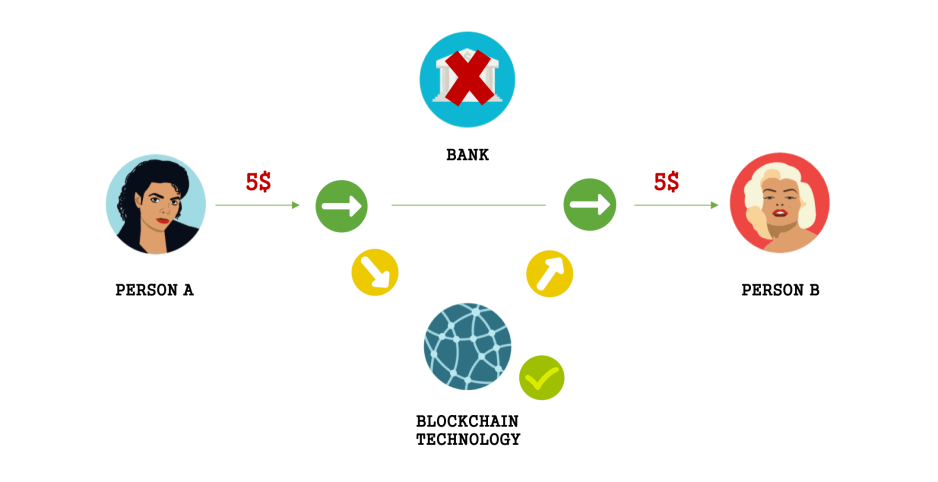
Fig 2: Blockchain Transaction
Case 2: In the above illustration (Fig 2), Person A initiates a transaction to transfer 5$ to Person B. Instead of going through a bank, the transaction here is being processed by the blockchain network. All the necessary checks and verifications that has to be done will be taken care by the blockchain network itself.
It is the same action that is being performed in both the scenarios above, but the means of doing it is different. If you consider a central authority like bank, there’ll be centralization of assets and information. This has its own share of downfalls like we discussed earlier. Since the blockchain is shared amonst everyone in the network, there’s more transparency to every transaction that occurs and the information once stored, cannot be changed or altered or even be removed.
It’s this immutability that makes the network transparent to everyone and also secure.
HOW DOES IT WORK?
What’s there in a Block?
Each block contains a definite amount of transactions and link to the previous block and this is what makes the blockchain chronological. Every block mandatorily contains the following:

Fig 3: Blockchain block
- Transaction details:
– Sender
– Receiver
– Transaction Amount - Hash:
– Identifies a block and all of its contents uniquely.
– Changing something inside the block will cause the hash to change - Hash of the Previous Block:
– This effectively creates a chain of blocks and it’s this technique that makes a blockchain so secure
The very first block is called the ‘GENESIS’ block with no transaction information and it cannot point to any previous blocks. It acts as a pointer to the entire blockchain.
What are Hashes?
Hashes are products of cryptographic algorithms and they manipulate data. Given an input, it forms an alphanumeric string of a fixed value. This is performed by the Hash Functions that converts data of arbitrary length to a fixed length. Every block in the blockchain uses these hash functions to encrypt its data hence making it secure and hard to decode. These hashes also act as a unique identifier.
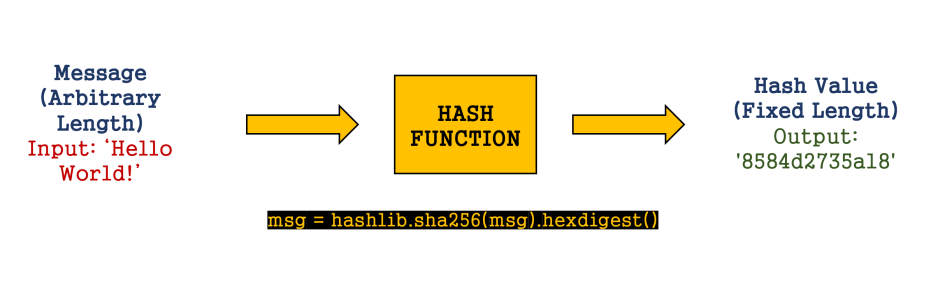
Fig 4: Hash Functions
The mentioned hash function ‘msg’ in the figure is a python library to create hash values.
The Blocks Chained
To chain a block to the network, each block must contain the solution to a complex mathematical problem created using a cryptographic hash function. Here is where the concept of Proof-Of-Work comes into play.
The Cryptographic hash function (similar to a puzzle) is irreversible and can only be solved by Brute Force. It typically takes a year for a single node (computer) in the network to solve the problem.
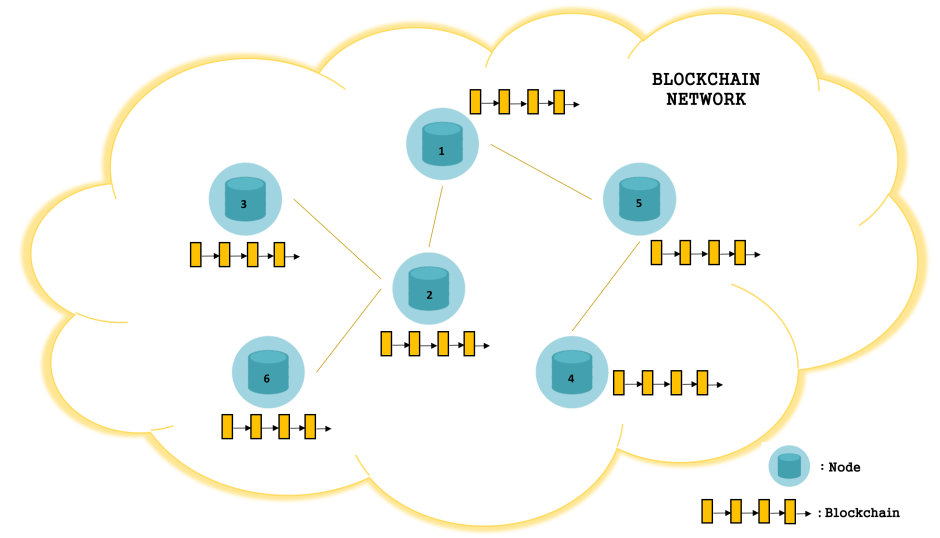
Fig 5: Blockchain Network
Every node in the blockchain network contains its own copy of the blockchain. This makes it a decentralized and a distributed network.
Whenever a node gets added to the Blockchain network, the node receives a wallet that allows it to perform transactions. The wallet would primarily consists of a public Key and a private Key and the hashes of a block are generated using these keys. When a transaction is initiated, the message first gets hashed using the private key, and then broadcasted across the entire network to all the peer nodes. The nodes that receive these transactions, decode the message using the public key and verify its legitimacy. Once verified, the nodes start solving the problem to find the correct answer. The nodes that solves the problem first shares the solution to all the other nodes in the network. The network verifies this Proof-Of-Work and if correct, the block will be added to the chain and the nodes that solved the problem receive a reward in return (Bitcoin in the Bitcoin blockchain). This is called “Mining a Block“.
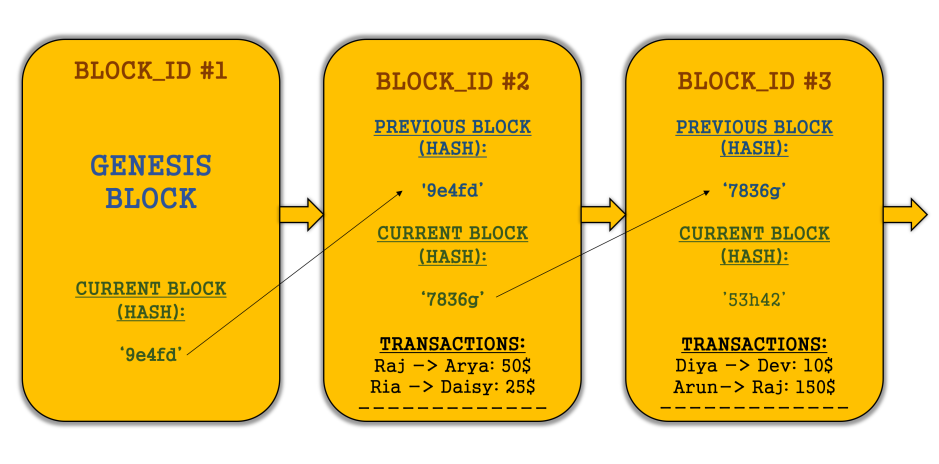
Fig 6: The Blockchain
Since mining a block requires a lot of computational power, nodes get together to solve the problem. In this way, it’s faster to solve a problem and the attained reward is shared amongst the participating nodes. Such groups are called as “Mining Pools“.
Understanding the Blockchain Trust Center
Let’s take an example to understand Proof-Of-Work:
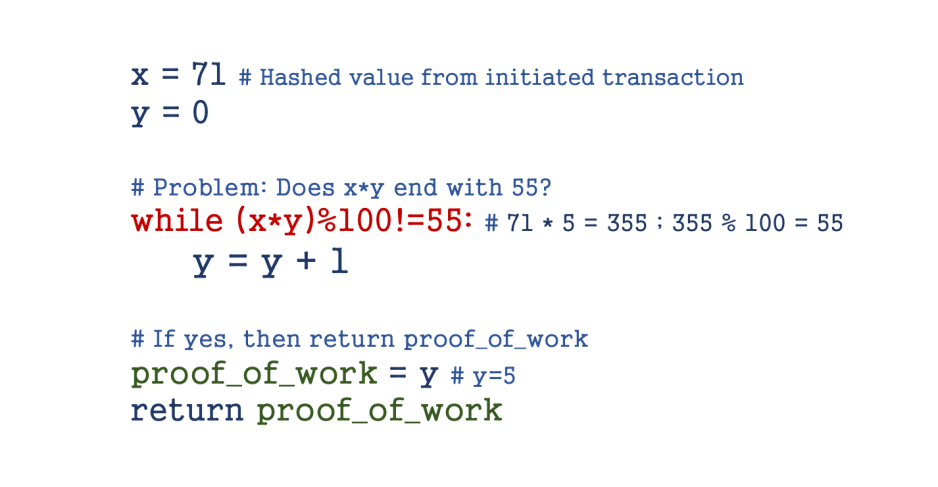
Fig 7: Proof-Of-Work Example
Assume ‘x’ is the hashed value from initiated transaction and ‘y’ is the value that decides the Proof-Of-Work solution. The above mentioned problem (Fig 7) doesn’t have the complexity of an actual cryptographic hash function but the underlying fundamentals remain the same.
The node that receives and picks up the transaction will start solving the cryptographic hash function to find the solution. In the above case, the solution is 5. It is easier to verify this solution than to decode to it. So, once this Proof-Of-Work is sent to the network, the other nodes can easily verify and agree that the mined block can be added to the chain. This implementation of cryptographic algorithms makes blockchain extremely secure.
In Conclusion…
Blockchain has not only changed the way we transact; but it also has revolutionized the internet. Right from security of data to transparency to immutability of its information, blockchain has a solid potential to be the game changer on the internet and many organizations are already moving in this direction. Although, even with such backing, blockchain has its share of drawbacks. It is environmentally flawed and it consumes high energy for every transaction and is also inefficient when it comes to performance.
Nonetheless, the Blockchain technology believes in decentralization of trust. This is the very concept of consensus – it trusts when majority of them say ‘Aye‘ and it rejects when they say ‘Nay‘. That’s where the beauty of it lies!
Now, having known the technology, would you say ‘Aye’ or ‘Nay’? If you’ve made a decision, then hold onto your choice. Only time will answer.

